Overview
The Admin Preferences page is the home page of the Admin section of ProVision where general platform preferences may be set.
To access it, click the gear icon at the top right section of the header. From there, select "Admin". You will then have access the Admin section tabs of ProVision, and will see the Admin Preferences page.
Video Walkthrough
Note: Video at applies to versions 6.0.0 to 7.0.0. For earlier versions, see Admin Preferences Page Overview (v5.1.0+) .
License Info
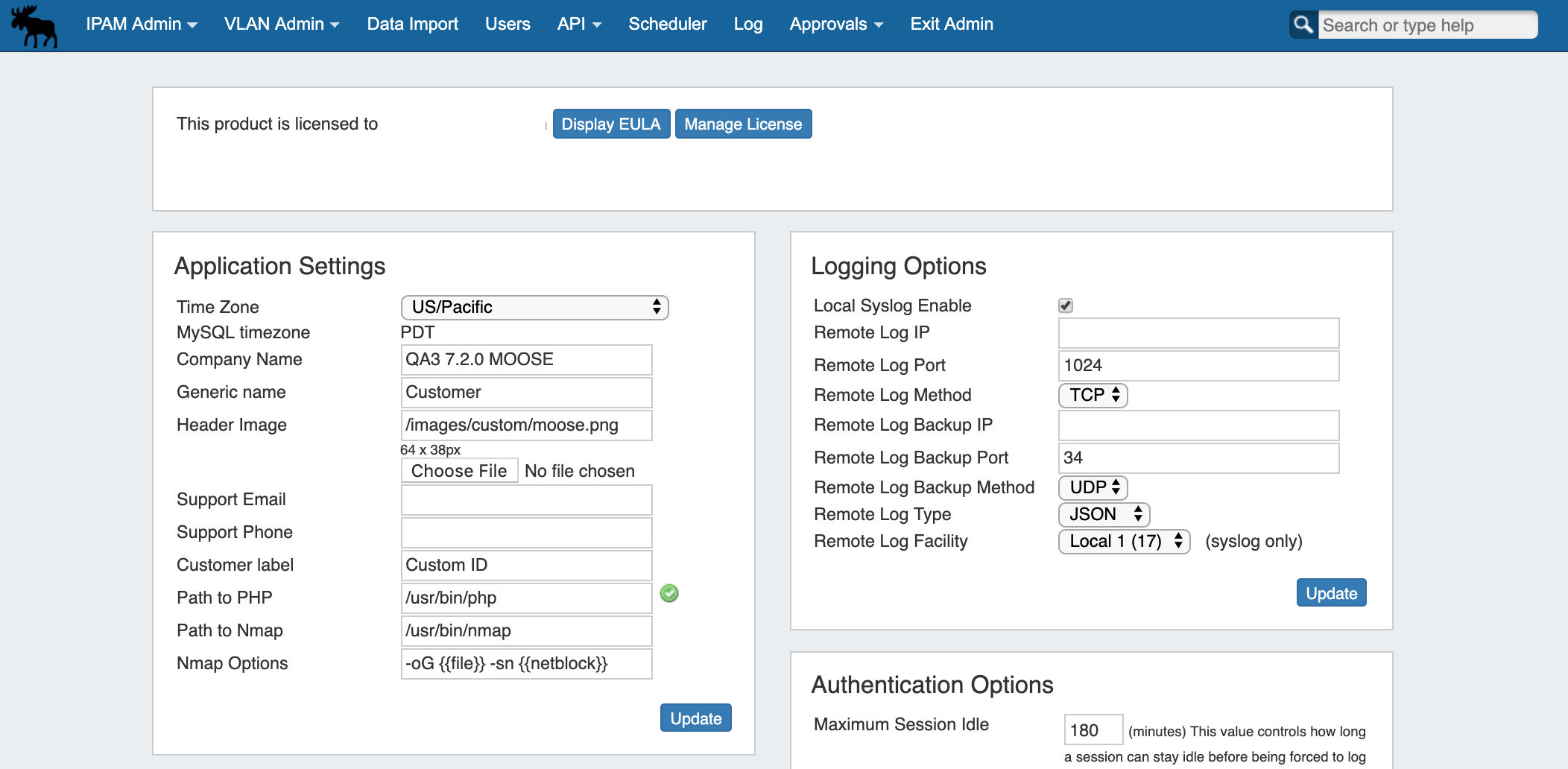
The License page displays current product license details such as Product, Type, Versions, Expiration, Email, and the option to add/update the 6connect License Key(s).
From the Admin Settings page, click "Manage License".
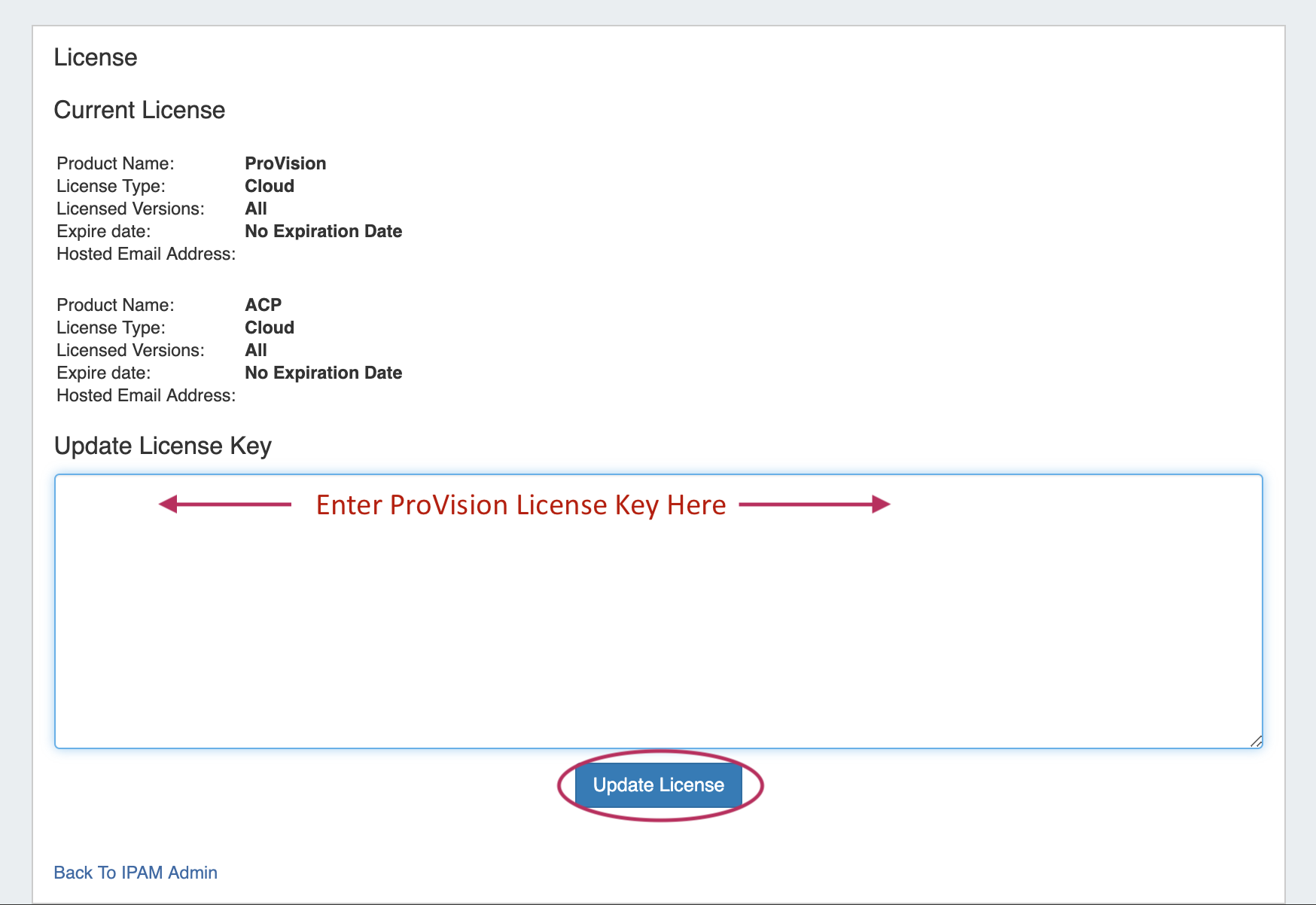
Current license details for ProVision, and other affiliated 6connect products will display.
To add/update a License Key, paste the key provided into the "Update License Key" box, and click "Update License".
Application Settings
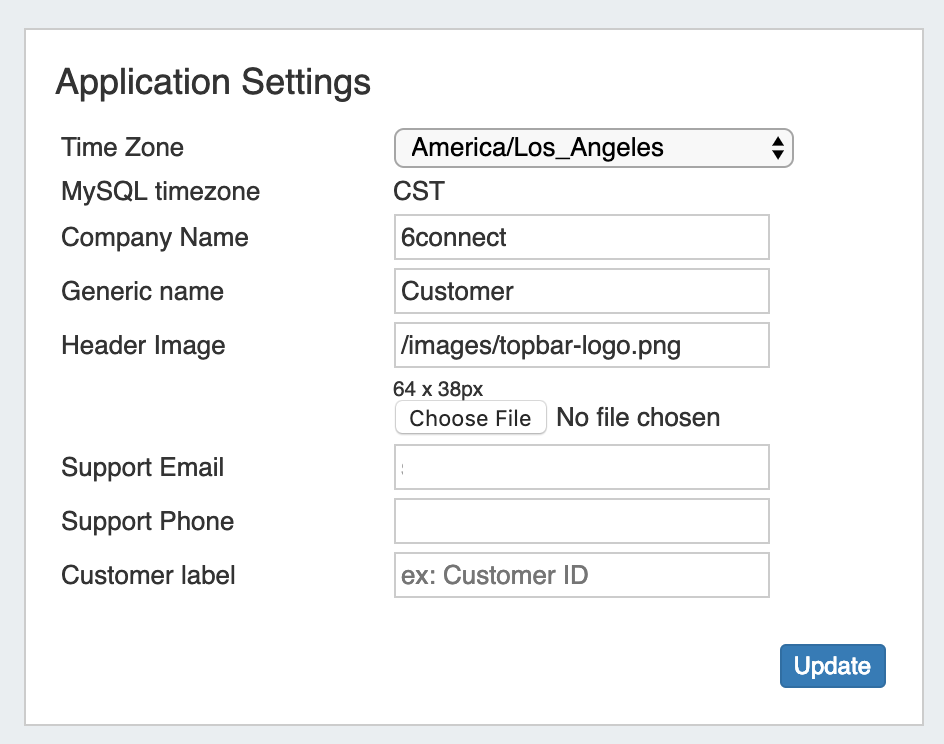
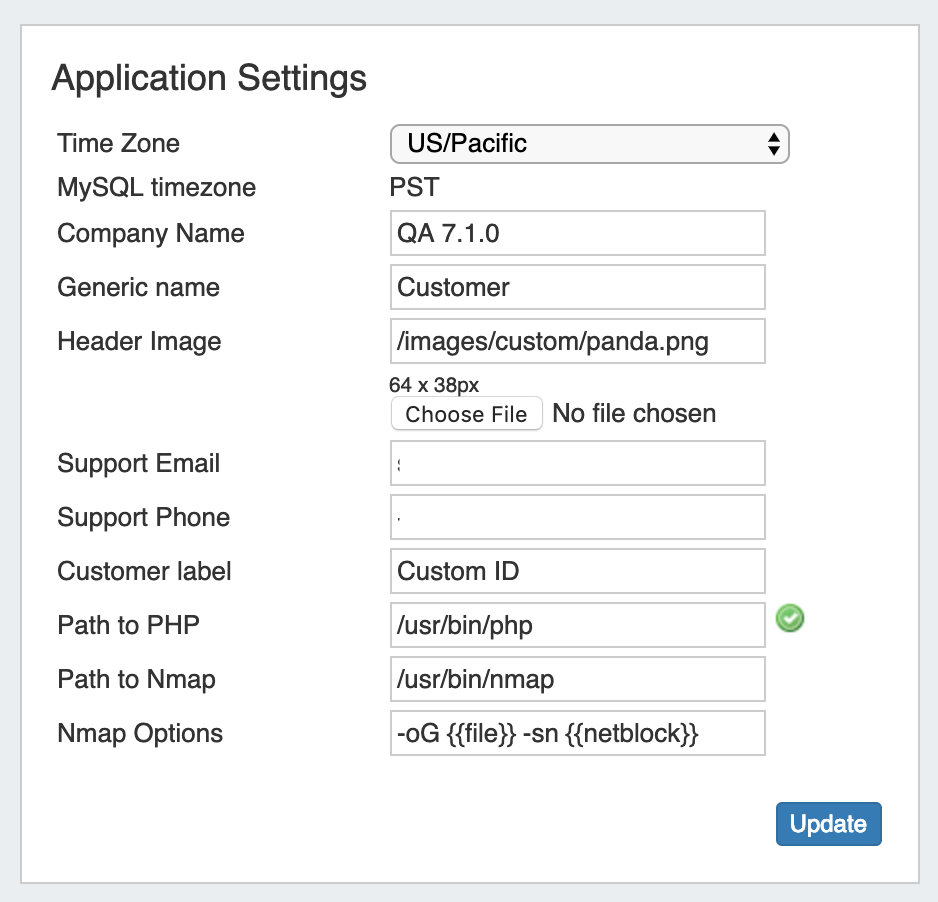
Application Settings is where you provide company specific info that appears in the header and Dashboard.
Time Zone: Supported Time zones are listed here: {EXT} http://www.php.net/manual/en/timezones.php. Default value is ('America/Los_Angeles') and can be modified at any time via the drop down menu
Company Name: Enter the preferred name for your company to be used.
Generic Name: This "short" name is used in abbreviated location for the "Customer" tab label, "Customer" and "Site" are common entries.
Header Image: Select an image file for the header
Support Email: Support Email address that displays on the Dashboard
Support Phone: Support phone number that displays on the Dashboard
Customer Label: The display name for the customizable label field available when creating or editing a resource.
Application Settings - Local Installation
Additional settings are available for local installations:
DNS Settings
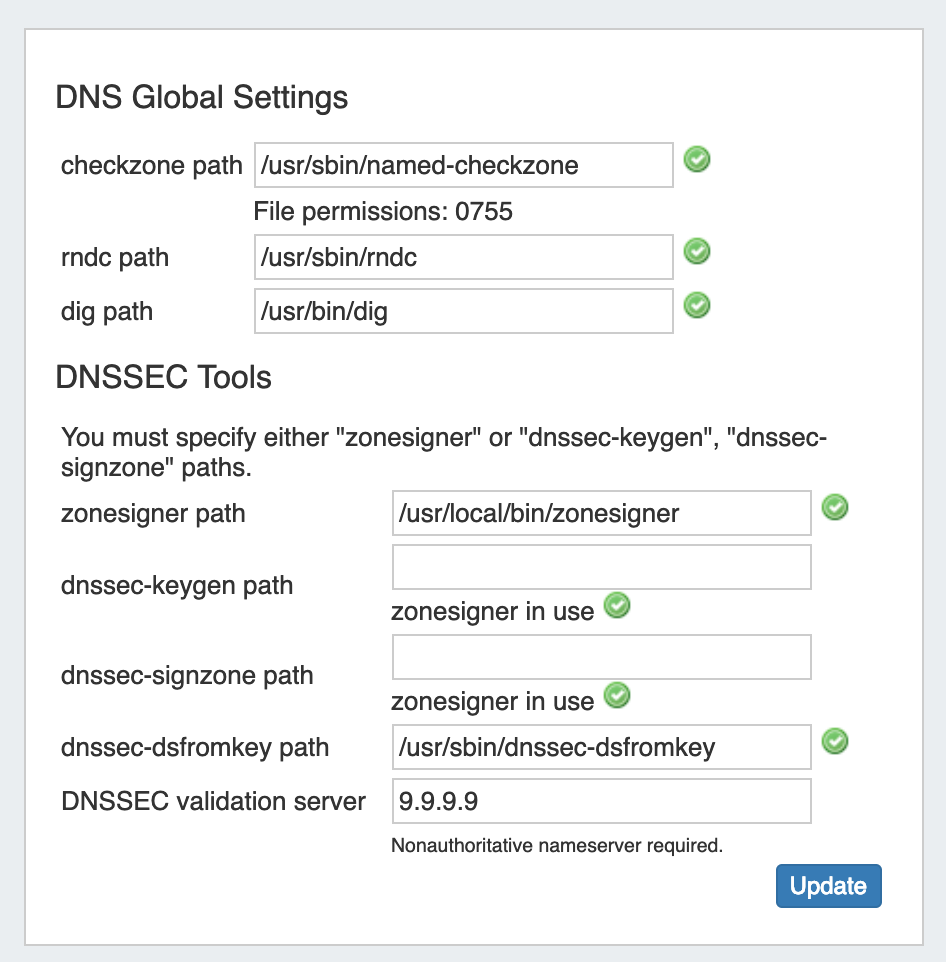
DNS Global Settings
Checkzone path : Enter the checkzone path that will be used for DNS.
rndc path : Enter the rndc path that will be used for DNS.
dig path : Enter the dig path that will be used for DNS.
DNSSEC Tools
If using DNSSEC, enter the following information:
zonesigner path : Enter the zonesigner path that will be used for DNS. Zonesigner is required if dnssec-keygen and dnssec-signzone are not set.
dnssec-keygen path: Enter the keygen path. Required if zonesigner is not set.
dnssec-signzone path: Enter the signzone path. Required if zonesigner is not set.
dnssec-dsfromkey path : Enter the dnssec-dsfromkey path that will be used for DNS. Required in all cases.
DNSSEC validation server: Enter the IP of the nonauthoritative DNSSEC validation nameserver. Optional.
Additional Entropy
If delays occur due to lack of available entropy on servers, see the following article on how to set up additional entropy using haveged here:
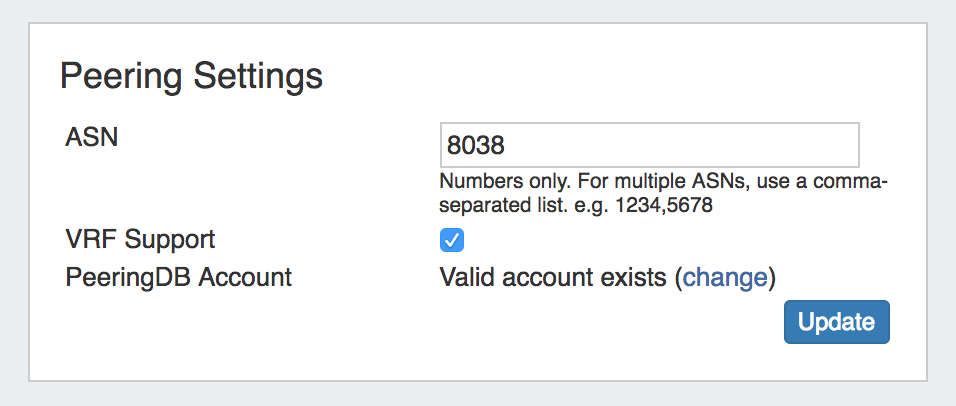
Peering Settings
ASN : Enter the ASN(s) that will be used for Peering, or may leave blank. Separate multiple ASNs with a comma.
VRF Support: Check to enable adding the VRF gadget to the router Section. Currently, only supports Cisco routers.
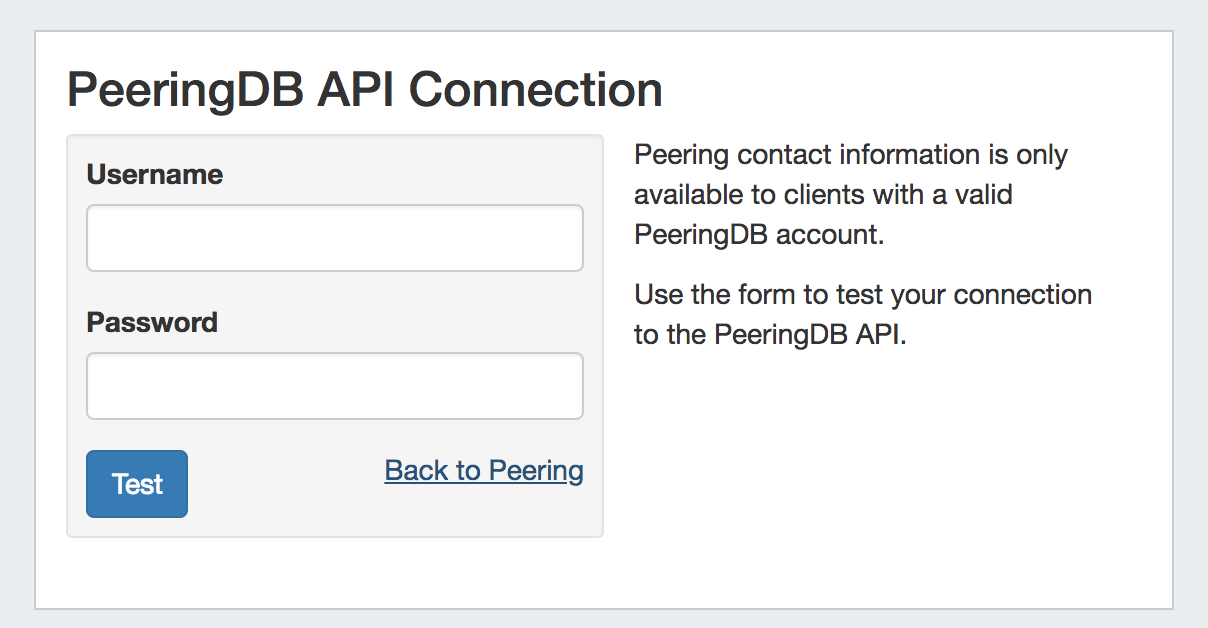
PeeringDB Account: Click the "change" link to input PeeringDB account credentials. PeeringDB account information is required to retrieve and update peering information.
Enter a valid PeeringDB account Username and Password. When done, click the "Test" button to verify the account, and save.
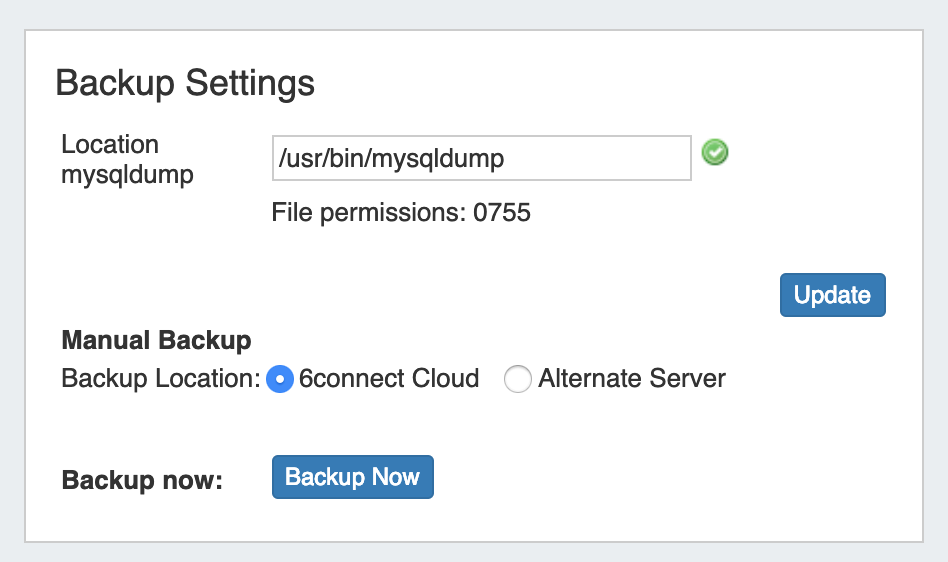
Backup Settings
For cloud users, regular backups can be set up through the Scheduler. However, prior to imports or other large changes, you may wish to manually perform a backup.
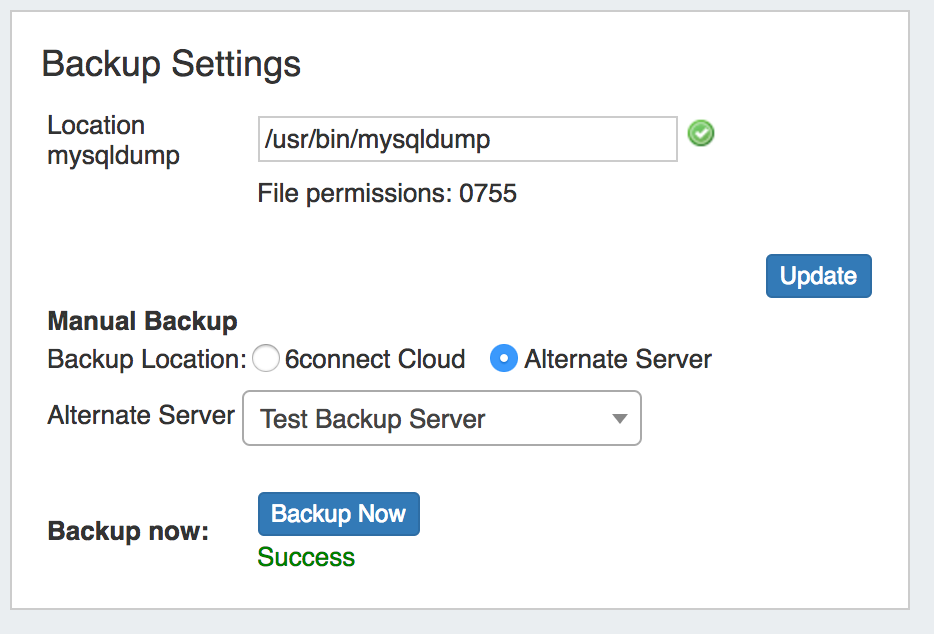
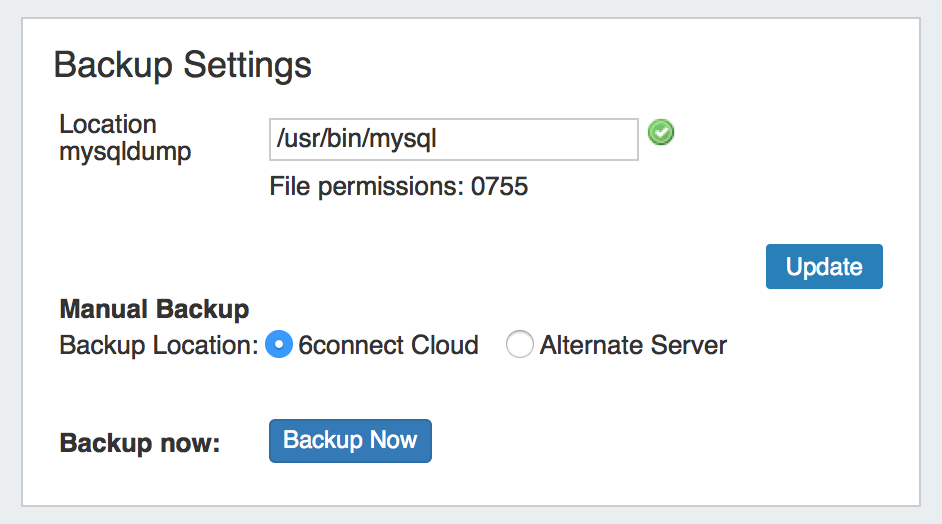
Backup Location: The backups may be sent to the 6connect cloud, or to a specific server in the Resource system. Select the radio button for the desired location.
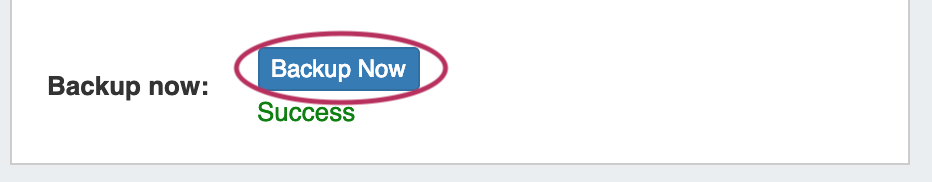
Manual Backup - 6connect Cloud:
Select "6connect Cloud" as your backup location, then click on the "Backup Now" button. You will see a success message below the button if successful.
Manual Backup - Alternate Server:
Manual Backup: Alternate Server saves a backup msql dump to a Server Resource already set up in ProVision.
This Resource needs to have the following information provided in the server section fields in order to establish a connection: Port, Hostname, Username, and Password.
Before selecting Alternate Server Backup:
1) Ensure that the Server Resource exists in ProVision for the backup (Section = "Server"). If needed, create a new entry for the server.
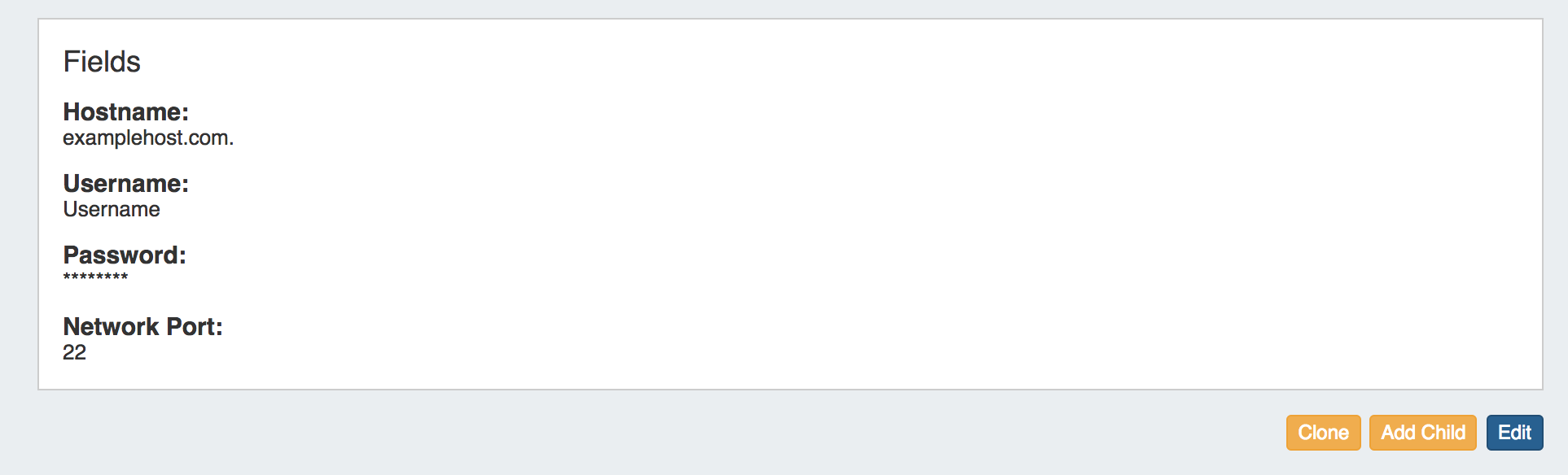
2) Check that the following fields are added to the Server Section:
- Network Port (22 is typical)
- Hostname (this can also be an IP address)
- Username
- Password
See Customizing Sections and Customizing Fields for information on adding fields to sections. Hostname, Username, Password, and Network Port will all be contained under the "Existing Fields" selector when adding fields to the Section.
3) On the Backup Server's Entry page, verify that the server fields are filled in and correct for the ProVision server entry:
If needed, click "Edit" and add or update the information. See Working with Entries for additional information.
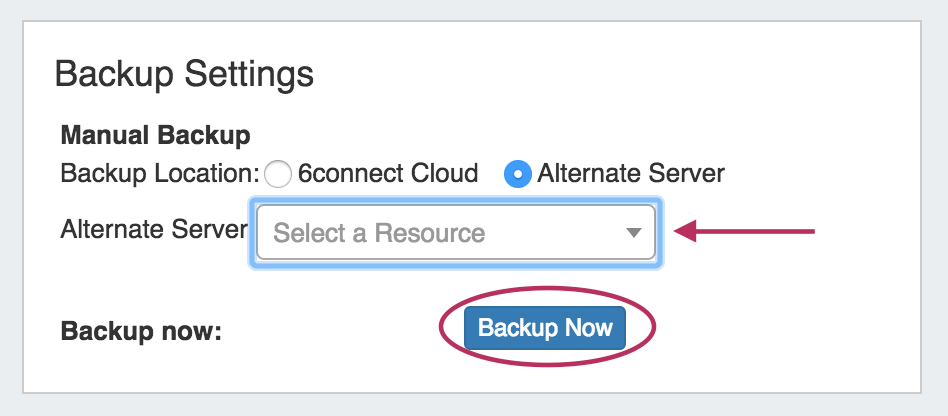
Once a Backup server has been set up in ProVision, it will be available to select under Backup Settings: Alternate Server.
Select "Alternate Server" as your backup location, then select the desired ProVision server Resource. After selecting your server, click on the "Backup Now" Button.
If successful, a mysql dump file will be sent to the selected server and a "Success!" message will appear.
Once the connection is confirmed successful, Backups to alternate servers may be scheduled on a recurring basis through the Scheduler Tab, or continued to be performed manually under Backup Settings.
Backup Settings - Local Installation
Additional settings are available for local installations:
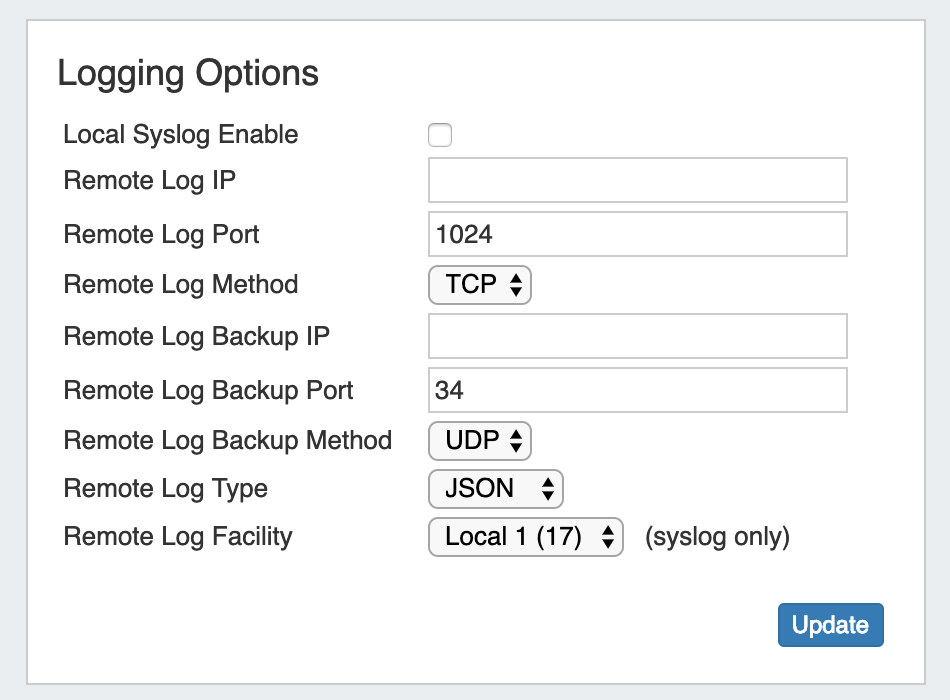
Logging Options
Remote Log IP: Target IP address that we will send log information to
Remote Log Port: Port number for the syslog server you will send log information to
Remote Log Method: Select TCP, UDP, SSL from the dropdown for the log delivery method
Remote Log Backup IP: Target IP address for the Backup syslog server you will send log information to
Remote Log Backup Port: Port number for the Backup syslog server you will send log information to
Remote Log Backup Method: Select TCP, UDP, SSL from the dropdown for the log delivery method
Remote Log Type: Select SysLog format or JSON output
Remote Log Facility: Select the Facility - applies to syslog only
Authentication Options
In this area, you may set the max session idle time, as well as setup additional authentication options.
Four authentication types are available for ProVision: Radius, LDAP, SAML, and DUO Mobile.
Session Time
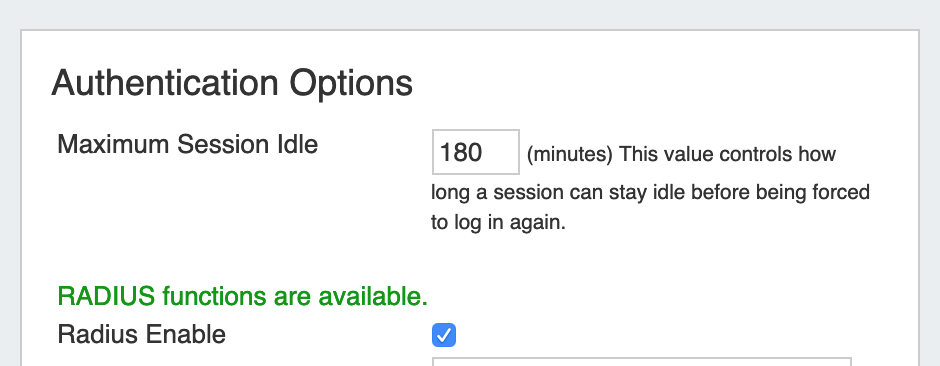
Maximum Session Idle: This setting (minutes) controls how long a session can stay idle before being forced to log in again.
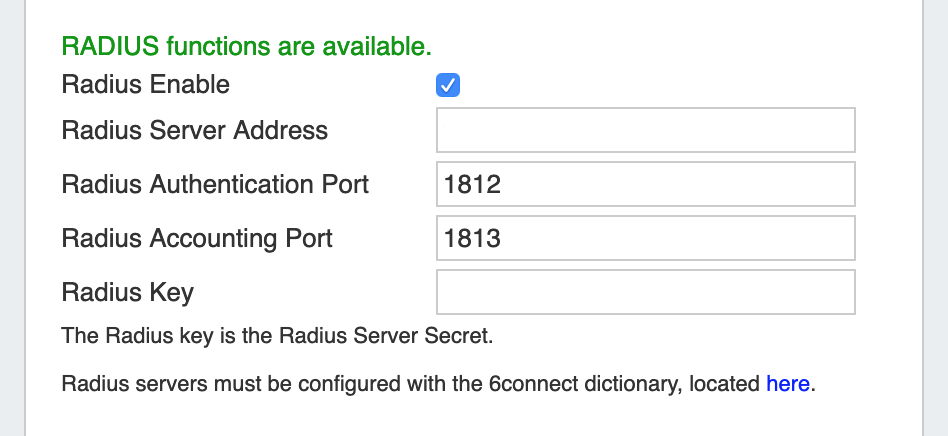
RADIUS authentication options (local install only)
Note: For implementation details, go here.
Radius Enable: Check this box to enable RADIUS functionality.
Radius Server Address: Set to the IP address of your radius server. If this is specified, it will force authentication over radius.
Radius Authentication Port: Set to the port for authentication. Default port is 1812
Radius Accounting Port: Set to the port for radius accounting. Default port is 1813
Radius Key: Set to the shared key of your radius server
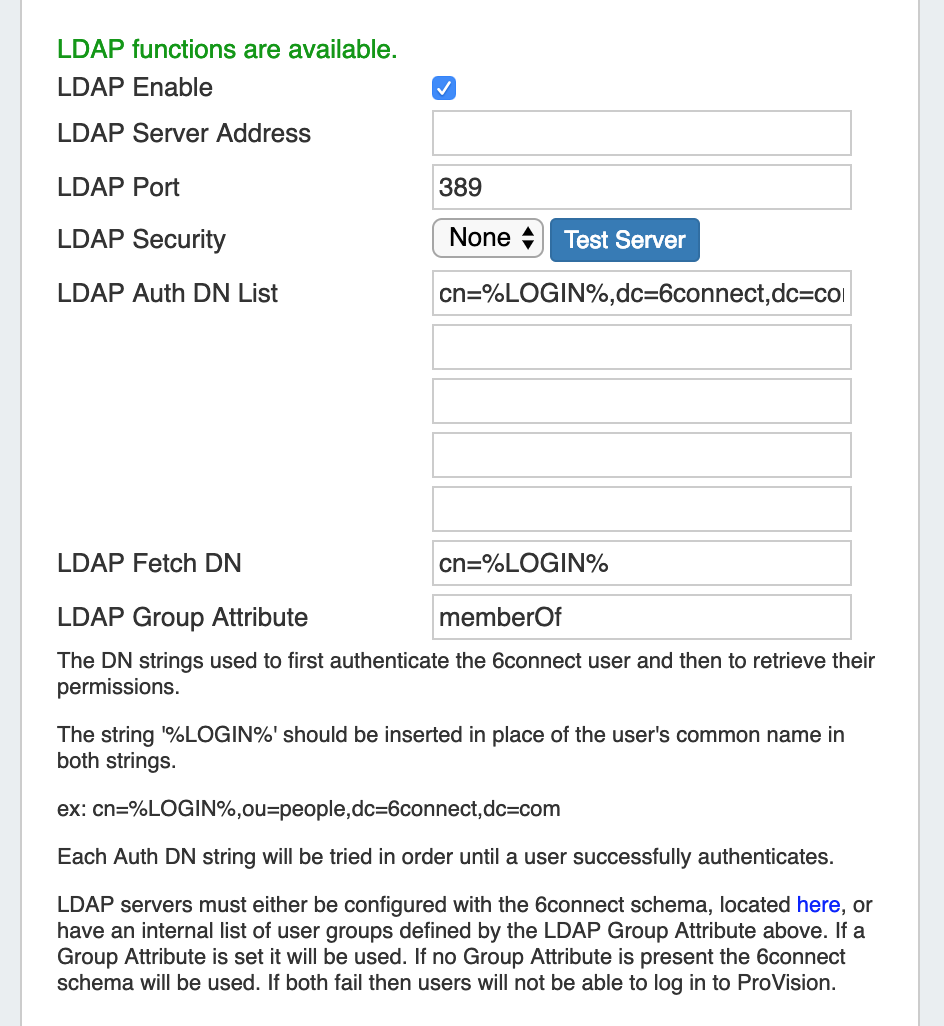
LDAP authentication
Note: For implementation details, go here.
LDAP Enable: check the box to enable LDAP functionality.
LDAP Server Address: Set the IP address of your LDAP server.
LDAP Port: Set the port for your LDAP server
LDAP Security: Select the security method of your LDAP server - SSL, TLS or None
Test Server: Click to test the connection to the LDAP server.
LDAP Auth DN/Fetch DN: These strings are used to first authentication the 6connect user and then to retrieve their permissions. The string '%LOGIN%' should be inserted in place of the user's common name both strings. (ex: cn=%LOGIN%,ou=people,dc=6connect,dc=com)
LDAP Group Attribute: If using an internal list of user groups instead of 6connect groups, enter the attribute name for the LDAP groups here. If a Group Attribute is set, it will be used first, otherwise the 6connect schema will be used.
Mapping Permissions to 6connect schema: To integrate 6connect permissions with your existing directory structure then you will need the 6connect schema. It should snap in with any existing LDAP structure and allow you to assign 6connect permissions to your existing users. You can download a copy of the schema from this section.
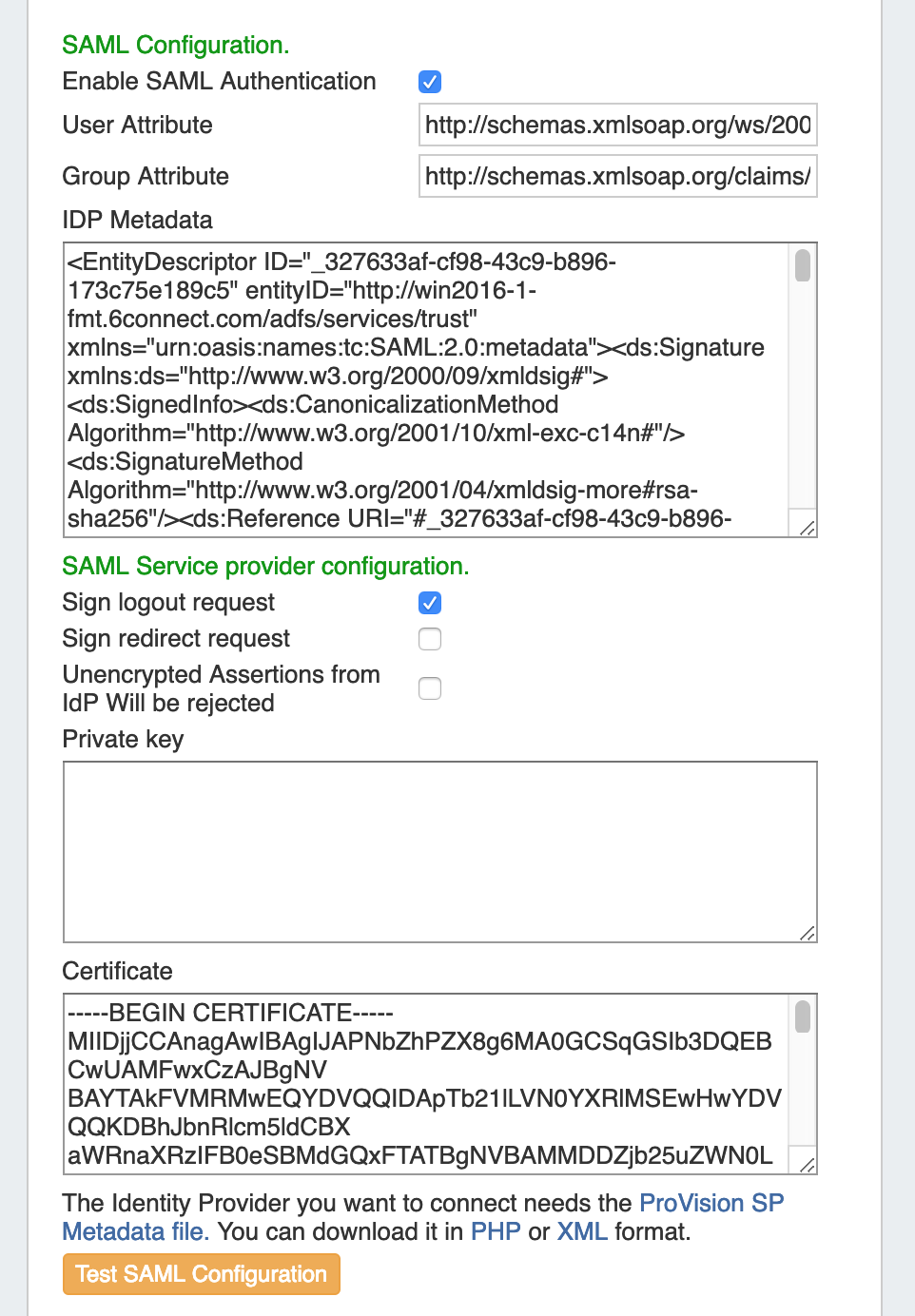
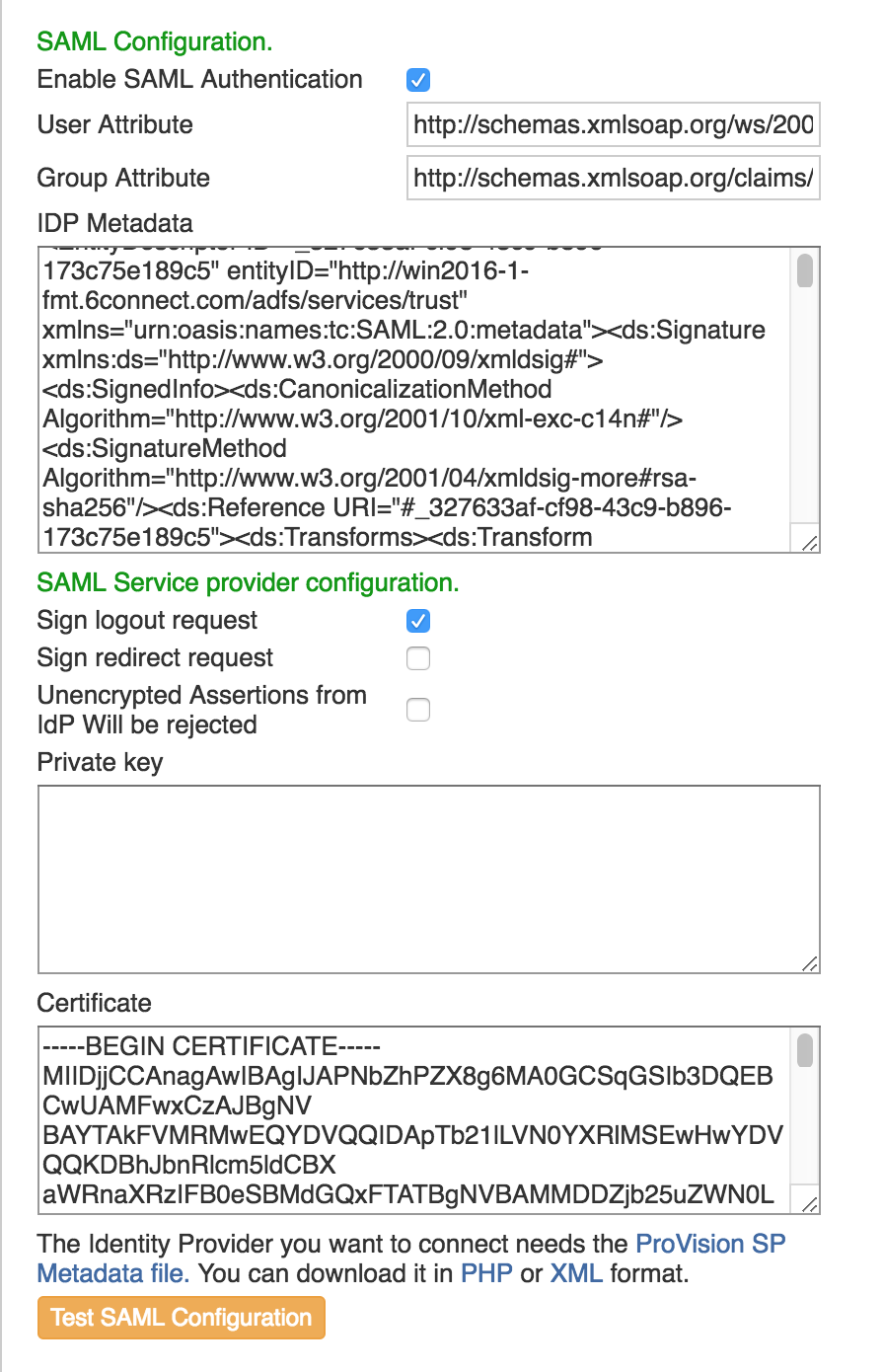
SAML authentication
SAML is a Single Sign On (SSO) authentication method that uses an external identity provider to authenticate a user at their first login, saving a token to the user's browser that is then used for subsequent logins, so that the user does not need to re-submit credentials.
SAML Setup
Before configuring SAML in ProVision, you must have an account set up with an Identity Provider (IdP) and ProVision users / groups set up in the IdP.
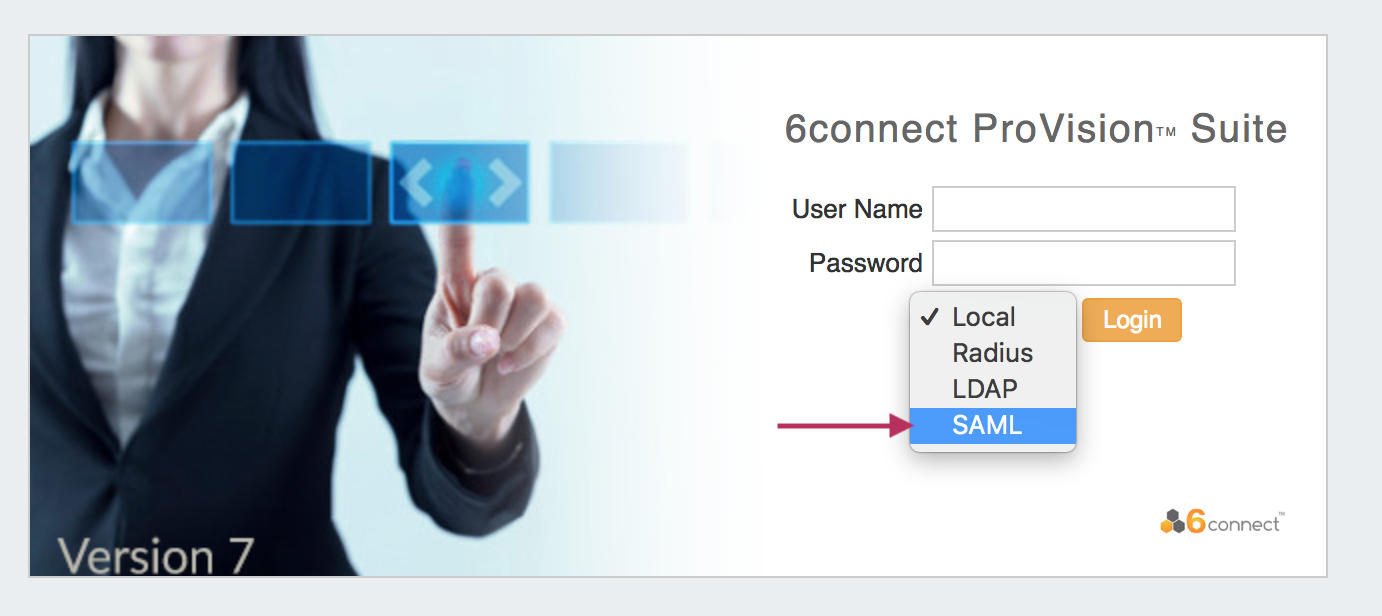
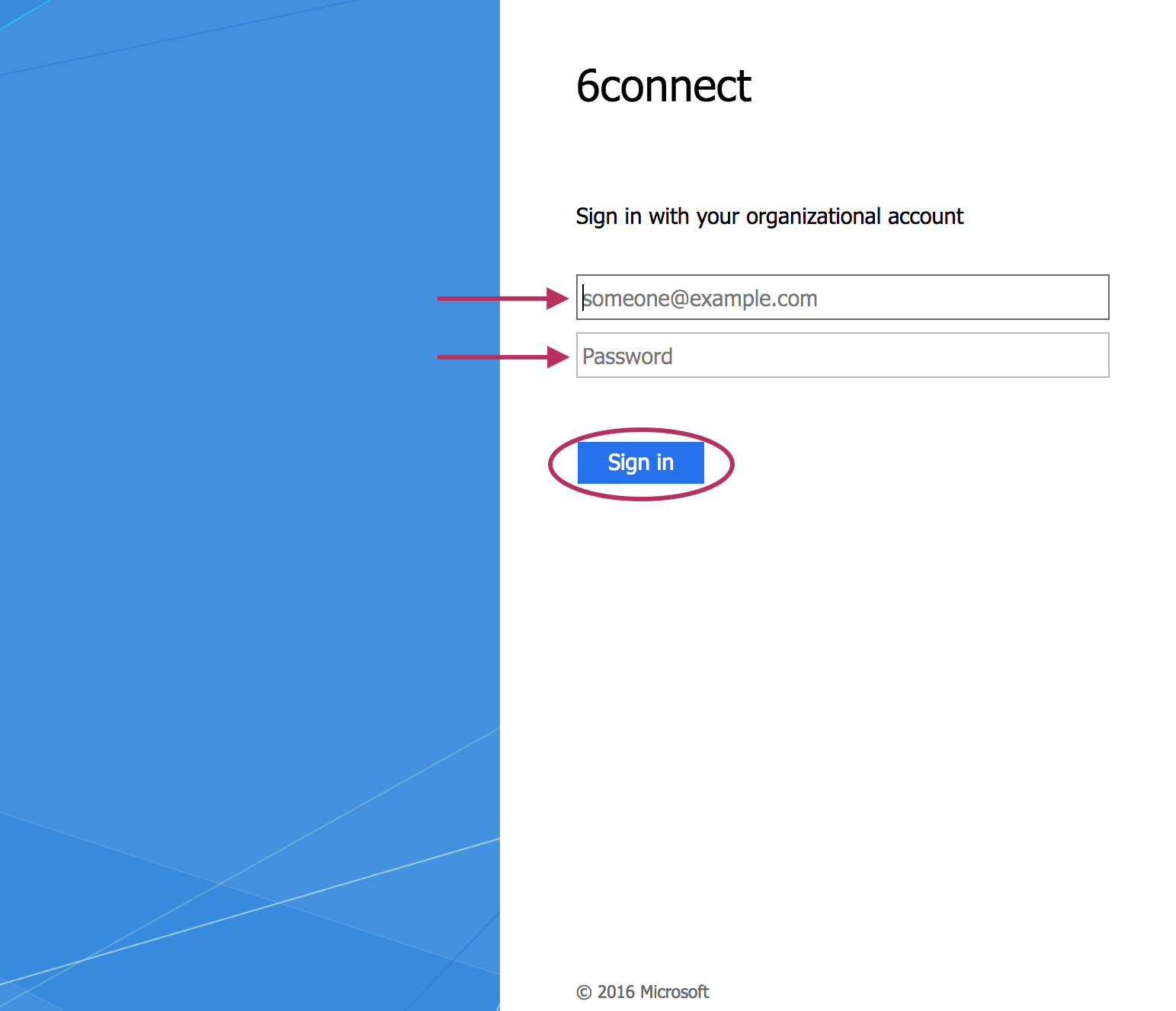
SAML Login
Once the correct configuration has been established and users set up for SAML in the IdP, users will be able to use SAML logins.
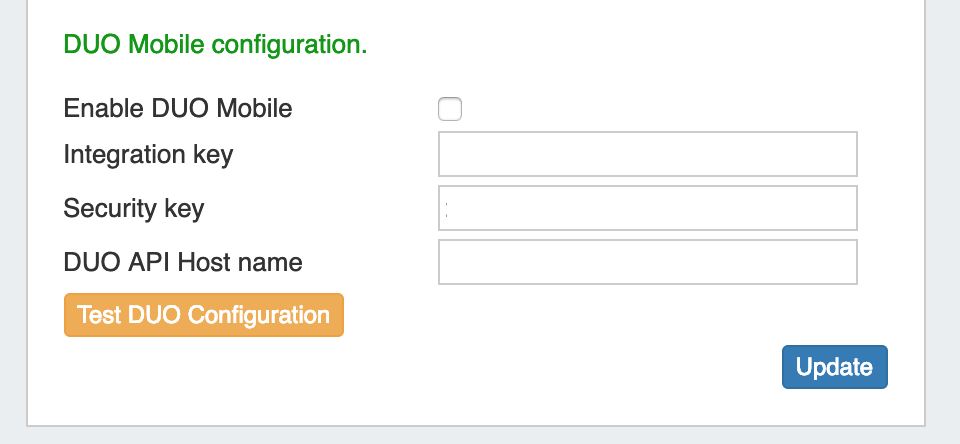
DUO Mobile
To use DUO Authentication, an account must first be set up with DUO.
Once an account is set up, obtain the Integration Key, Security Key, and DUO API Host name.
Enter those items into Admin→ Authentication Options → DUO Mobile Configuration, and click "Update" to save your changes.
You may also test the current configuration by clicking "Test DUO Configuration".
If you need to disable DUO Mobile authentication from ProVision from outside of the GUI, a command-line disable tool is available. Run:
php tools/disable_duo.php
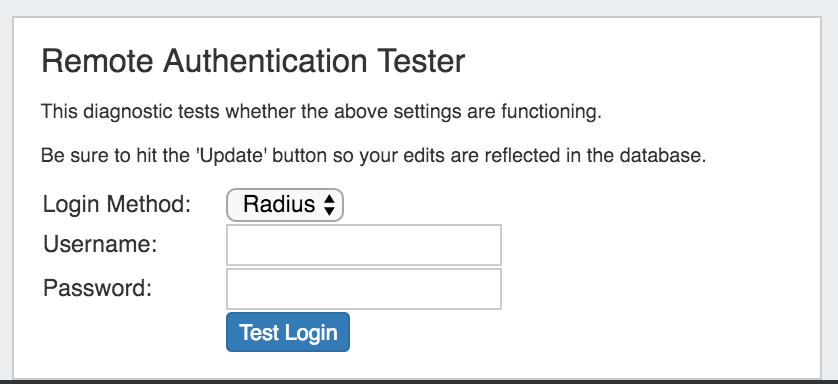
Remote Authentication Tester
The Remote Authentication Tester checks Radius / LDAP settings for a user.
Select the Login Method (Radius or LDAP), enter the Username and Password for the user, and then click "Test Login".
Login Method: Select Radius or LDAP, according to your authentication settings.
Username: The username for the user you are testing.
Password: Password for the user you are testing.
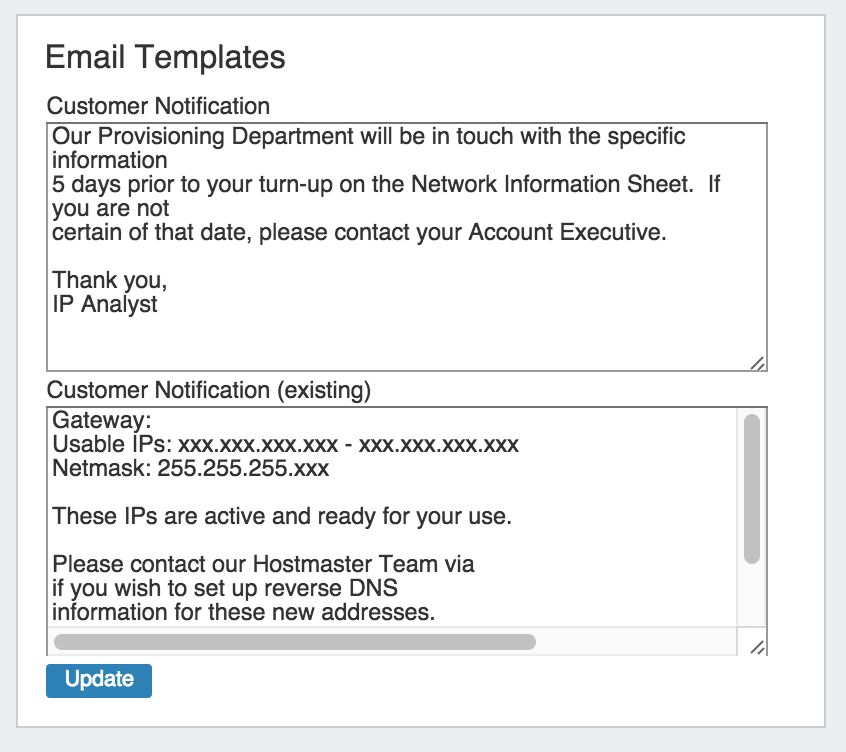
Templates
This is where you can edit outgoing email templates for IP block assignments.
To edit, click inside the text area box, make the desired changes, then click the "Update" button.
After making changes to settings, clicking any "Update" button will save your changes for all sections of the page, not just the section the update button is contained in.