RADIUS Authentication
Starting in 3.0, ProVision supports 6connect vendor-specific attributes (VSAs) for use with RADIUS authentication.
To use these attributes, you must perform the following procedures:
| Table of Contents |
|---|
Setting Up Radius Authentication
Add the 6connect VSA to the Radius Installation
To use the 6connect VSA, the attributes must be defined on the RADIUS server. Add the following RADIUS dictionary file to your RADIUS server and name it dictionary.6connect:
Important Note: Between version 3.9.3 and 4.0, the permissions structure for ProVision was significantly changed. Make sure you following the version specific instructions below.
ProVision 3.9.3 and prior:
...
| title | 3.9.3 VSA text file |
|---|
...
ProVision 4.0 and greater:
...
| Code Block |
|---|
VENDOR 6connect 36009
BEGIN-VENDOR 6connect
ATTRIBUTE 6connect_user_group 10 string
#A 6connect User Group to which this user belongs.
END-VENDOR 6connect |
| Note |
|---|
| Make sure to add the following to the primary dictionary file: $INCLUDE dictionary.6connect |
Configure Radius Accounts
On the Radius server, configure the user accounts that will have access to the ProVision system.
An example of a ProVision account configuration for the user file on a Freeradius system for version 3.9.3 and prior:
| Code Block |
|---|
#A user with full IPAM prvileges and view only DNS privs
joe Cleartext-Password := "testing128"
priv_admin = 1,
priv_ipam_v = 1,
priv_ipam_c = 1,
priv_ipam_d = 1,
priv_ipam_m = 1,
priv_swip = 1,
priv_email = 1,
priv_dns_v = 1 |
An example of a ProVision account configuration for the user file on a Freeradius system for version 4.0 and greater:
Example: To To add a new radius user, edit the 'users' file found at /etc/raddb/users and add a block like:
| Code Block | ||||
|---|---|---|---|---|
| ||||
bobber Cleartext-Password := "hello" 6connect_user_group = "Global Admins,Group 2,Group 1,Group Nonexistent"Nonexistant" |
The Radius server must be restarted every time you add, remove, or modify users. To restart the Radius server, use this command:
| Code Block |
|---|
/etc/init.d/radiusd restart |
| Note | ||
|---|---|---|
| ||
| There are many Radius attributes, but '6connect_user_group' is the one used by 6connect ProVision and it . It is just a comma-separated list of all the group names that the user belongs to. |
Test Radius Accounts
For 3.9.3 and priorProVision 4.0 and higher, test and response should look like the following:
To query a radius server, use the following command format:
| Code Block | ||||
|---|---|---|---|---|
| ||||
radtest [USERNAME] [USERPASSWORD] [SERVER] 0 [SECRET] |
Example:
| Code Block |
|---|
radtest bobber hello 208.39.140.106 0 6connect |
A successful response will look like this:
| Code Block | ||
|---|---|---|
| ||
#>radtest test test 50.23.215.162 6connect Sending Access-Request of id 179198 to 50208.2339.215140.162106 port 1812 User-Name = "testbobber" User-Password = "testhello" NAS-IP-Address = 1067.124221.47240.6229 NAS-Port = 0 Message-Authenticator = 0x00000000000000000000000000000000 rad_recv: Access-Accept packet from host 50208.2339.215104.162106 port 1812, id=179198, length=69 Attr-10 =68 priv_admin = 1 priv_ipam_c = 1 priv_ipam_m = 1 priv_ipam_d = 1 |
For 4.0 and higher, test and response should look like the following:
...
0x476c6f62616c2041646d696e732c47726f757020322c47726f757020312c47726f7570204e6f6e6578697374616e74 |
A rejected response may look like this:
| Code Block | ||
|---|---|---|
| ||
Sending Access-Request of id 68 to 208.39.140.106 port 1812
User-Name = "bobberbro"
User-Password = "hello"
NAS-IP-Address = 67.221.240.229
NAS-Port = 0
Message-Authenticator = 0x00000000000000000000000000000000
rad_recv: Access-Reject packet from host 208.39.104.106 port 1812, id=68, length=20 |
Configure ProVision for Radius Authentication
To configure the use of Radius authentication with ProVision, follow the steps below.:
- Log into 6connect ProVision
- Go to
...
- Settings → Admin -> Authentication
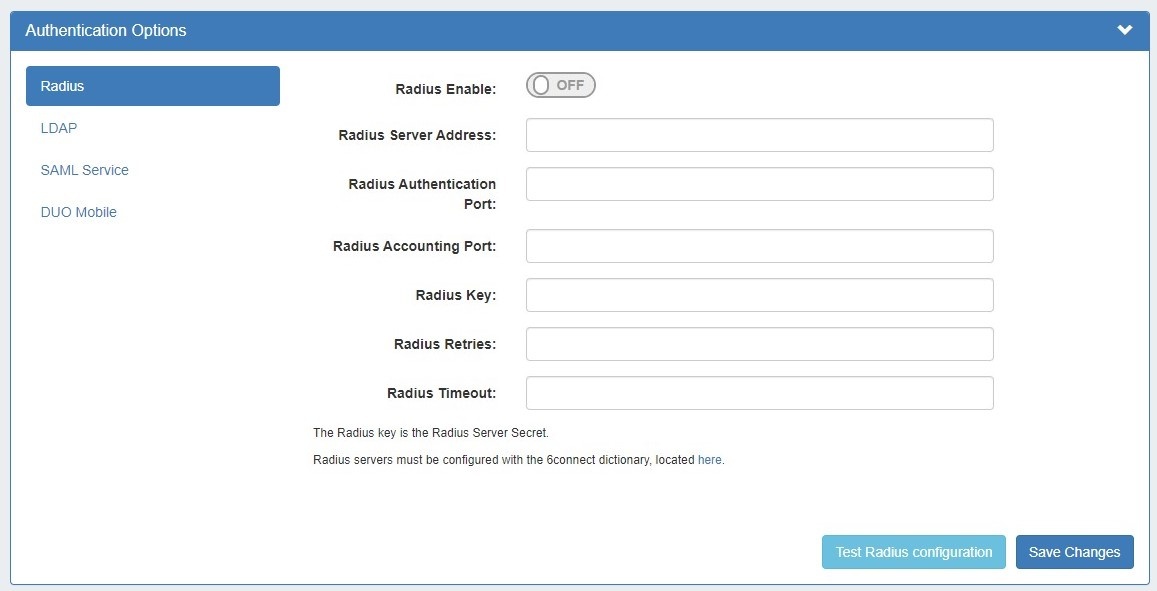
- Select the "Radius" tab under "Authentication Options"
- Ensure that Radius functions are
...
- available. Radius functions are always available on 6connect cloud instances.
...
- Note: Radius functions are available on VM Images and Local Installations only if the relevant PHP Pear Radius Libraries have been installed. An error message will be visible if the PHP extension is not installed.
...
- Move the Radius Enable
...
- selector to the "ON" position.
- Fill in the hostname or ip address, authentication ports, accounting port, and shared Radius key as specified.
| Expand | ||
|---|---|---|
| ||
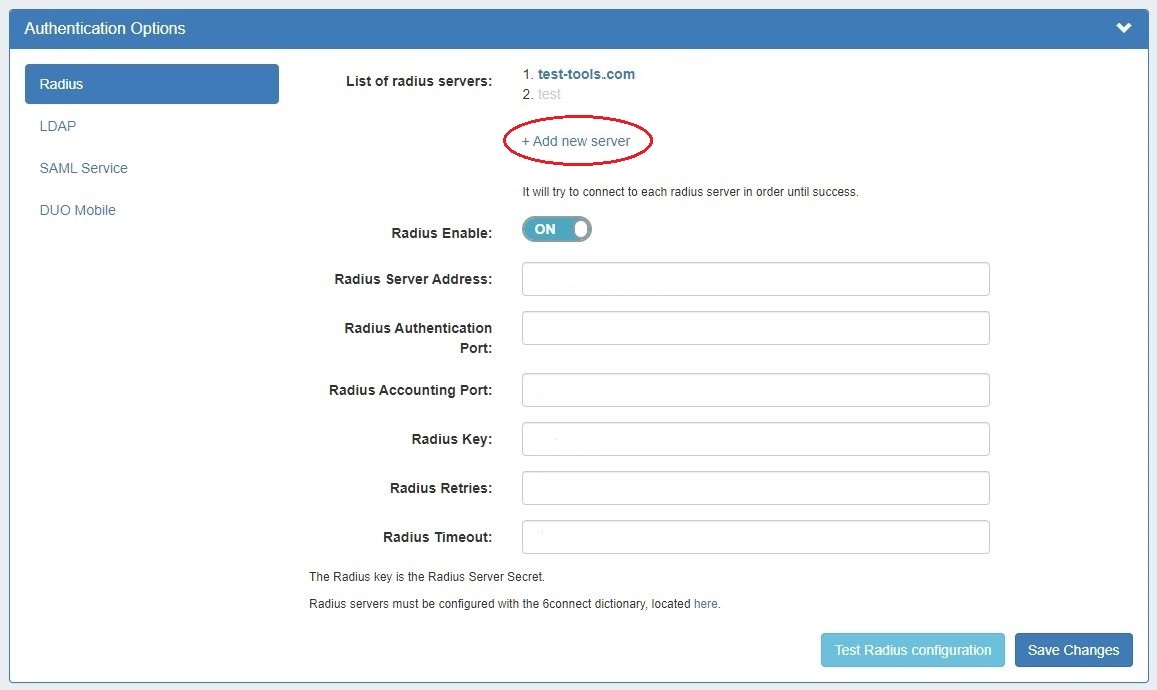
Once at least one Radius server has been added, a list will appear at the top of the Radius module. Add an additional Radius server by clicking "Add new server". ProVision will try to connect to each radius server listed in the order listed, until a success is returned. Disabled servers will display in grey, and the currently selected server will display in bold. |
| Note | ||
|---|---|---|
| ||
In the login screen, you would select the authentication method from the dropdown. If you like, you can set the default login option in the following way: Go to the /data/globals.php and open in vi (or other editor). Add in the following text as the last line of the file (before the closing ?﹥>) define('DEFAULT_LOGIN_TYPE', 'radius'); |
Add or Update Radius Authentication Settings (Local Install Only)
Authentication options are accessed by clicking the "Authentication" sub-tab at the top of the Admin Settings page.
- Radius Enable: Move this selector to enable RADIUS functionality.
- Radius Server Address: Set to the IP address of your radius server. If this is specified, it will force authentication over radius.
- Radius Authentication Port: Set to the port for authentication. Default port is 1812
- Radius Accounting Port: Set to the port for radius accounting. Default port is 1813
- Radius Key: Set to the shared key of your radius server
Enter or update the desired settings.
To verify the settings connect, click "Test Radius Configuration". When done, click "Save Changes".